Migrate docs for Access control (#4249)
Also `Creating sample user`.
Showing
docs/images/overview.png
0 → 100644
162.4 KB
68.5 KB
docs/images/signin.png
0 → 100644
44.9 KB
Also `Creating sample user`.
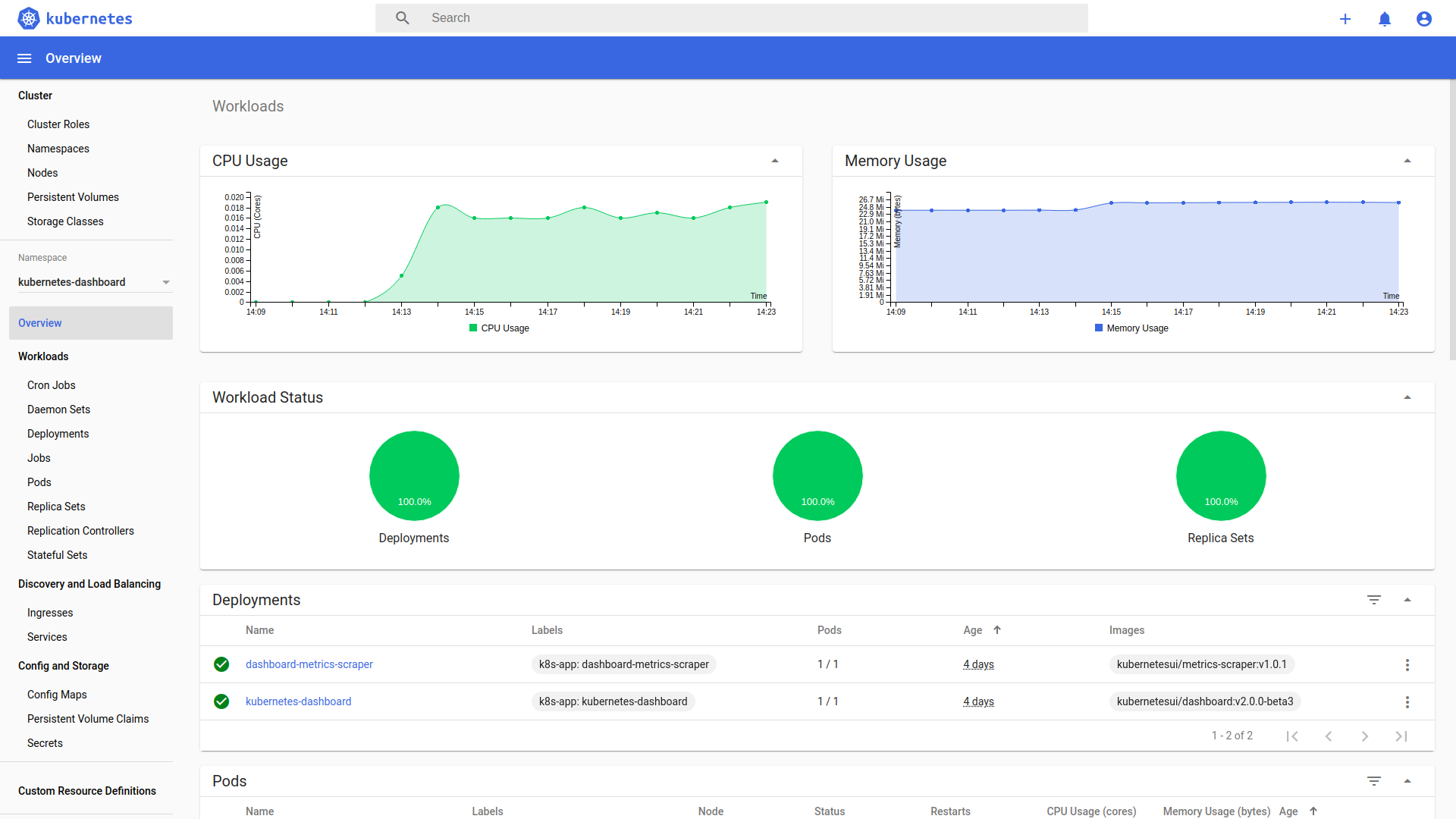
162.4 KB
68.5 KB
44.9 KB
