!8803 翻译完成:7600 新增3.2beta2 changelog
Merge pull request !8803 from wusongqing/TR7600
Showing
32.8 KB
38.2 KB
14.1 KB
30.9 KB
15.4 KB
19.5 KB
45.9 KB
6.4 KB
Merge pull request !8803 from wusongqing/TR7600
32.8 KB
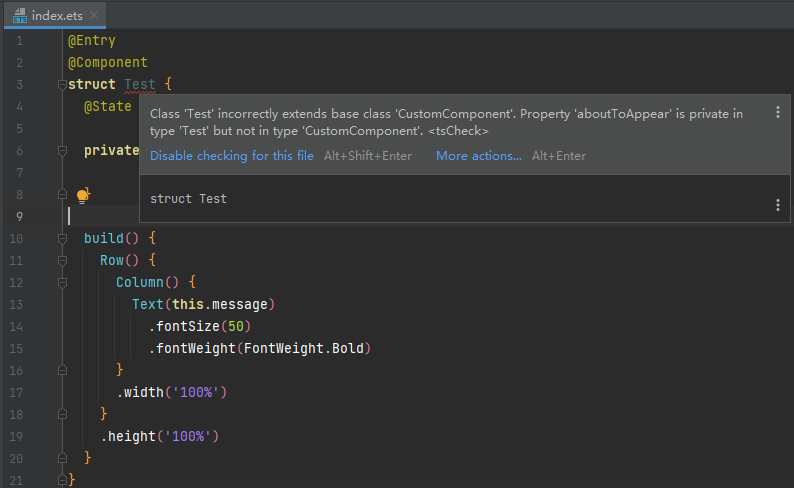
38.2 KB
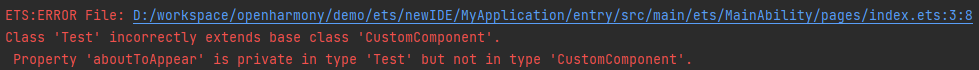
14.1 KB
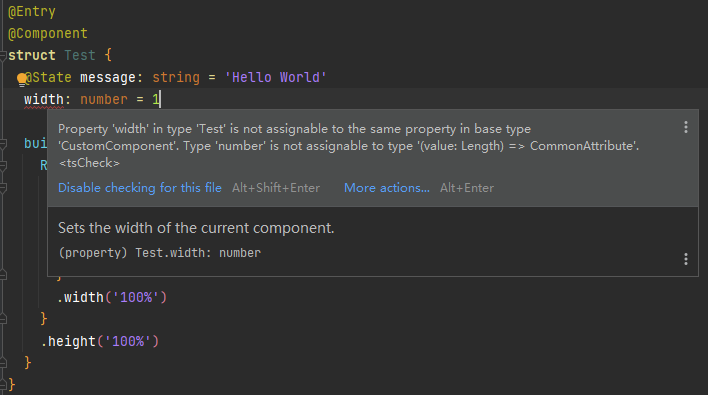
30.9 KB
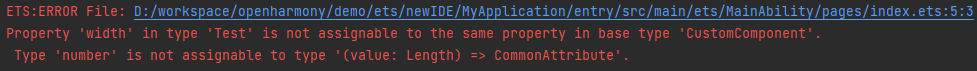
15.4 KB
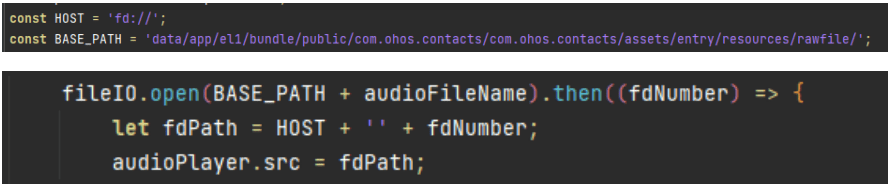
19.5 KB
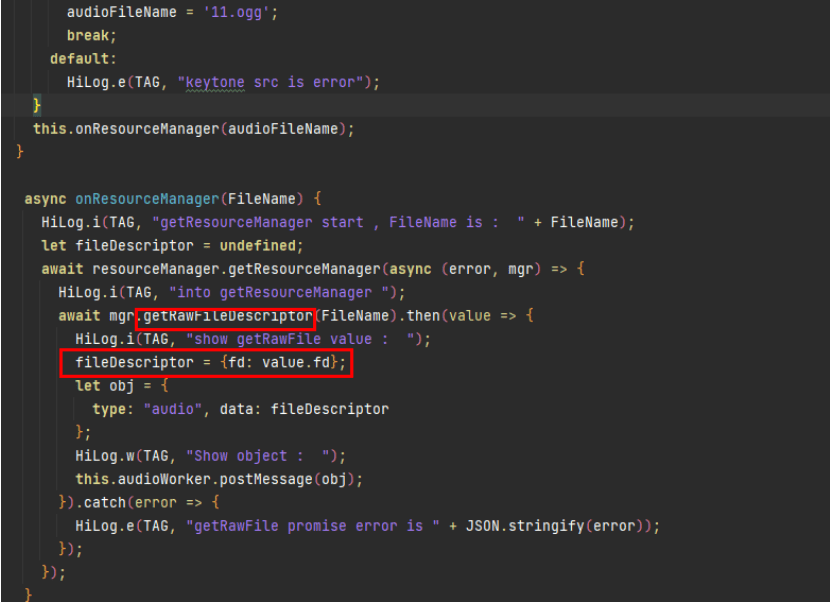
45.9 KB
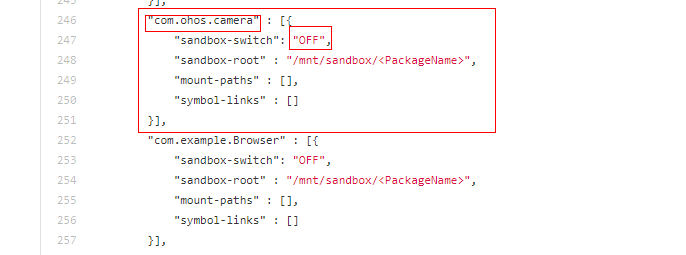
6.4 KB
