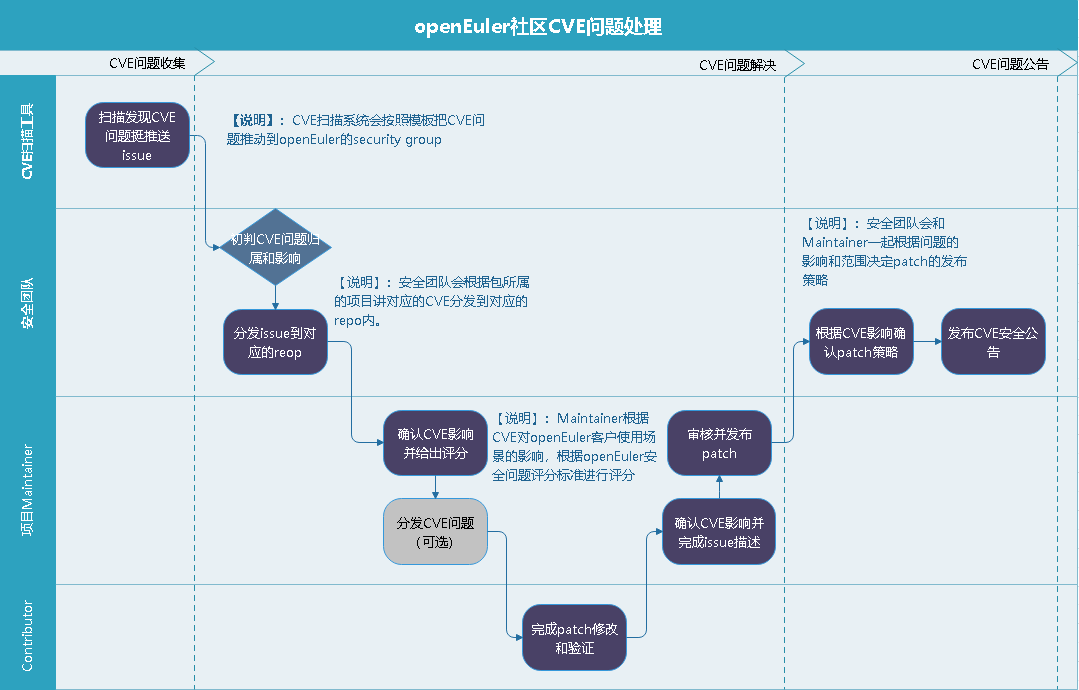
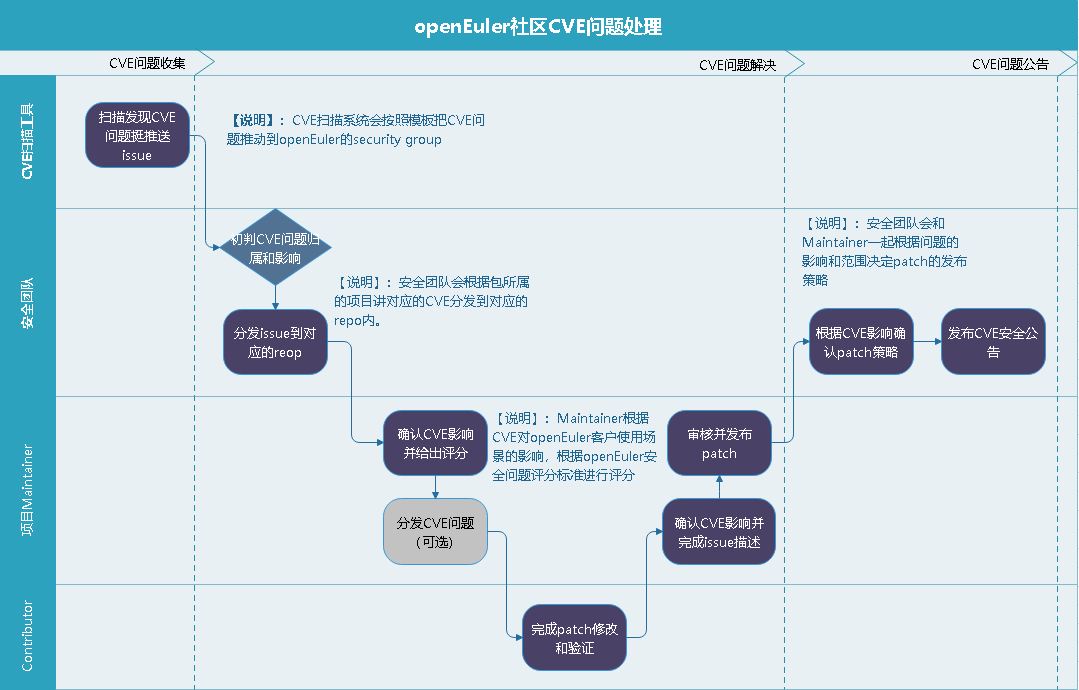
!23 Add introduction about security procedure
Merge pull request !23 from Fred_Li/master
Showing
content/en/security/index.md
0 → 100644
文件已添加
content/en/security/procedure.png
0 → 100644
39.0 KB
content/zh/security/index.md
0 → 100644
文件已添加
content/zh/security/procedure.png
0 → 100644
39.0 KB