Inclavare Containers
Introduction
inclavare-containers is a set of tools for running trusted applications in containers with the hardware-assisted enclave technology. Enclave, referred to as a protected execution environment, prevents the untrusted entity from accessing the sensitive and confidential assets in use.
Components
rune
rune is a CLI tool for spawning and running enclaves in containers according to the OCI specification. The codebase of rune is a fork of runc, so rune can be used as runc if enclave is not configured or available.
rune currently supports the Linux platform with x86-64 architecture only. It must be built with Go version 1.14 or higher.
rune depends on protobuf compiler. Please refer to this guide to install it on your platform. Additionally, rune by default enables seccomp support as runc so you need to install libseccomp on your platform. Note that the libseccomp is also required in container environment, and the host version should be equal or higher than the one in container.
# create $WORKSPACE folder
mkdir -p "$WORKSPACE"
cd "$WORKSPACE"
git clone https://github.com/alibaba/inclavare-containers
cd inclavare-containers/rune
# install Go protobuf plugin for protobuf3
go get github.com/golang/protobuf/protoc-gen-go@v1.3.5
# build and install rune
make
sudo make installrune will be installed to /usr/local/sbin/rune on your system.
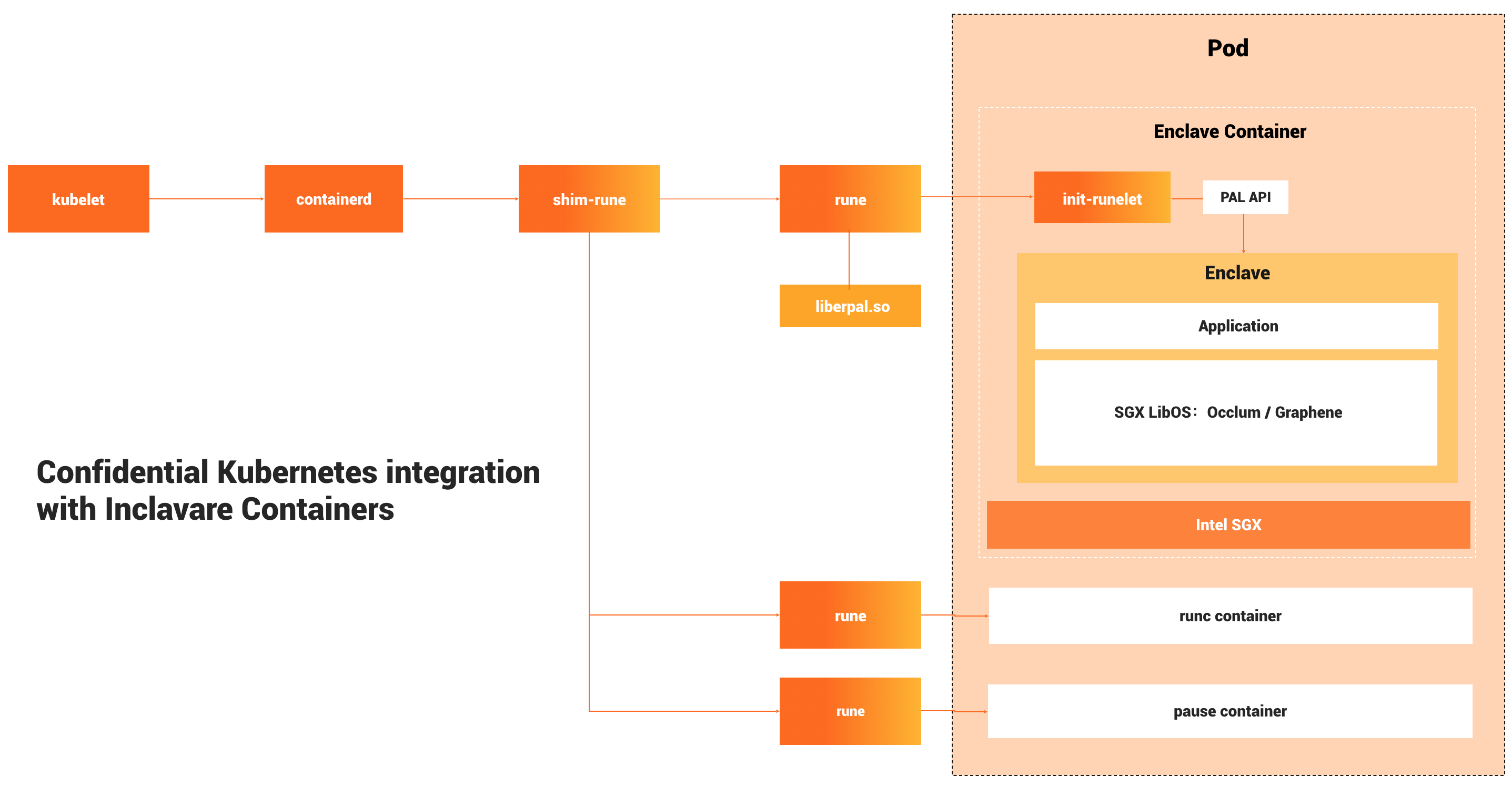
shim-rune
shim-rune resides in between containerd and rune, conducting enclave signing and management beyond the normal shim basis. shim-rune and rune can compose a basic enclave containerization stack for the cloud-native ecosystem. Please refer to this guide for the details.
enclave runtime
The backend of rune is a component called enclave runtime, which is responsible for loading and running protected applications inside enclaves. The interface between rune and enclave runtime is Enclave Runtime PAL API, which allows invoking enclave runtime through well-defined functions. The software for confidential computing may benefit from this interface to interact with OCI runtime.
One typical class of enclave runtime implementations is based on library OSes. Currently, the default enclave runtime interacting with rune is Occlum, a memory-safe, multi-process library OS for Intel SGX.
In addition, you can write your own enclave runtime with any programming language and SDK (e.g, Intel SGX SDK) you prefer as long as it implements Enclave Runtime PAL API.
sgx-tools
sgx-tools is a commandline tool, used to interact Intel SGX aesm service to retrieve various materials such as launch token, Quoting Enclave's target information, enclave quote and enclave remote attestation report from IAS. Refer to this guide for the details about its usage.
Terminology
Please refer to this doc for the details.
Using rune
Run Occlum
Please refer to this guide to run Occlum with rune.
Run skeleton
Skeleton is an example of enclave runtime, interfacing with Enclave Runtime PAL API for easy interfacing with rune. Skeleton sample code is helpful to write your own enclave runtime.
Please refer to this guide to run skeleton with rune.
Run OCI bundle
Please refer to this guide to run occlum bundle with rune.
Run rune containers in Kubernetes cluster
Please refer to this guide to develop and deploy a rune container in a Kubernetes cluster.
Reference container image
The reference container images are available for the demonstration purpose to show how a Confidential Computing Kubernetes Cluster with Inclavare Containers works. Currently, web application demos based on OpenJDK 11, Dragonwell, and Golang are provided.