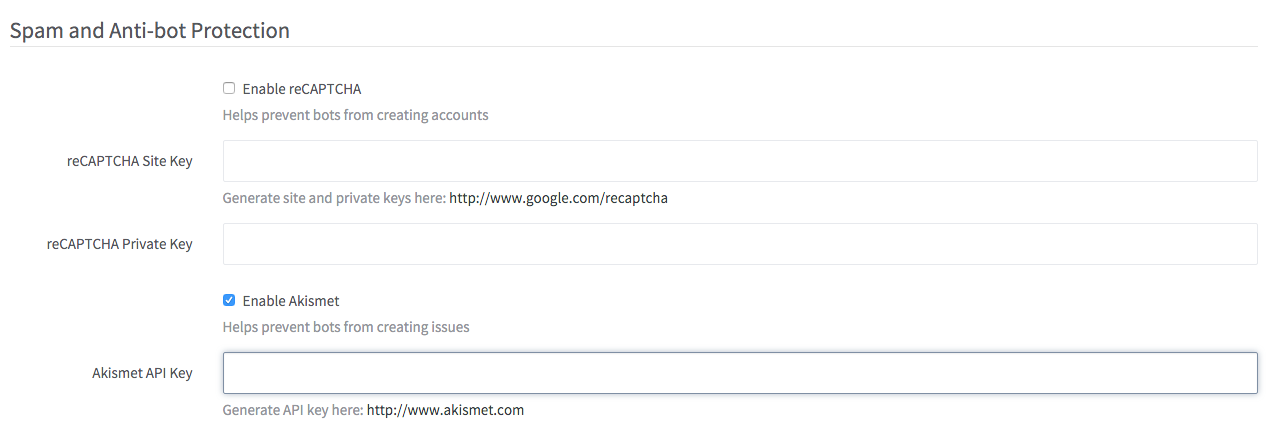
Support Akismet spam checking for creation of issues via API
Currently any spam detected by Akismet by non-members via API will be logged in a separate table in the admin page. Closes #5612
Showing
| ... | ... | @@ -36,8 +36,9 @@ gem 'omniauth-twitter', '~> 1.2.0' |
| gem 'omniauth_crowd', '~> 2.2.0' | ||
| gem 'rack-oauth2', '~> 1.2.1' | ||
| # reCAPTCHA protection | ||
| # Spam and anti-bot protection | ||
| gem 'recaptcha', require: 'recaptcha/rails' | ||
| gem 'akismet', '~> 2.0' | ||
| # Two-factor authentication | ||
| gem 'devise-two-factor', '~> 2.0.0' | ||
| ... | ... |
app/models/spam_log.rb
0 → 100644
app/models/spam_report.rb
0 → 100644
doc/integration/akismet.md
0 → 100644
54.5 KB
features/admin/spam_logs.feature
0 → 100644
features/steps/admin/spam_logs.rb
0 → 100644
lib/gitlab/akismet_helper.rb
0 → 100644
spec/factories/spam_logs.rb
0 → 100644