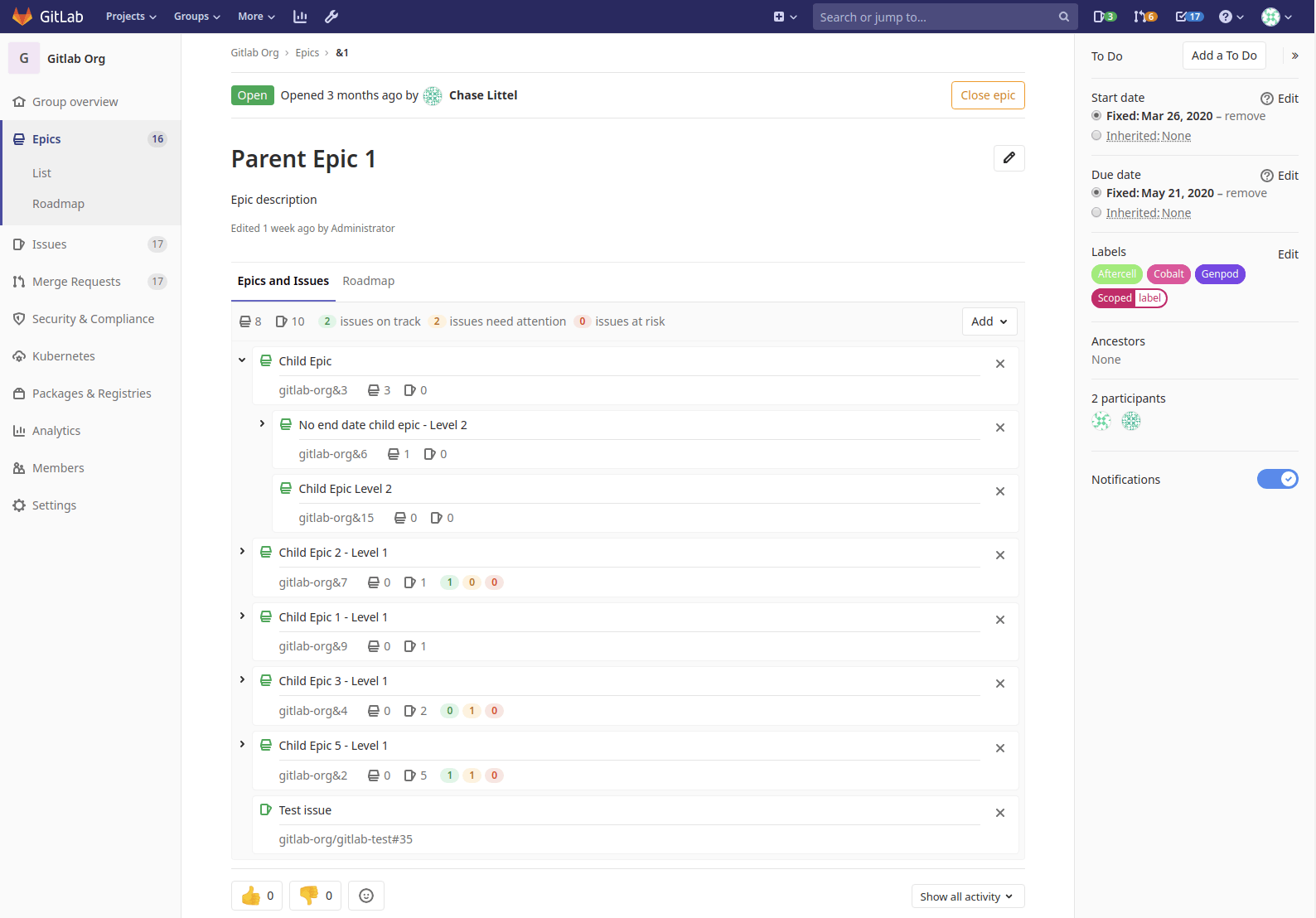
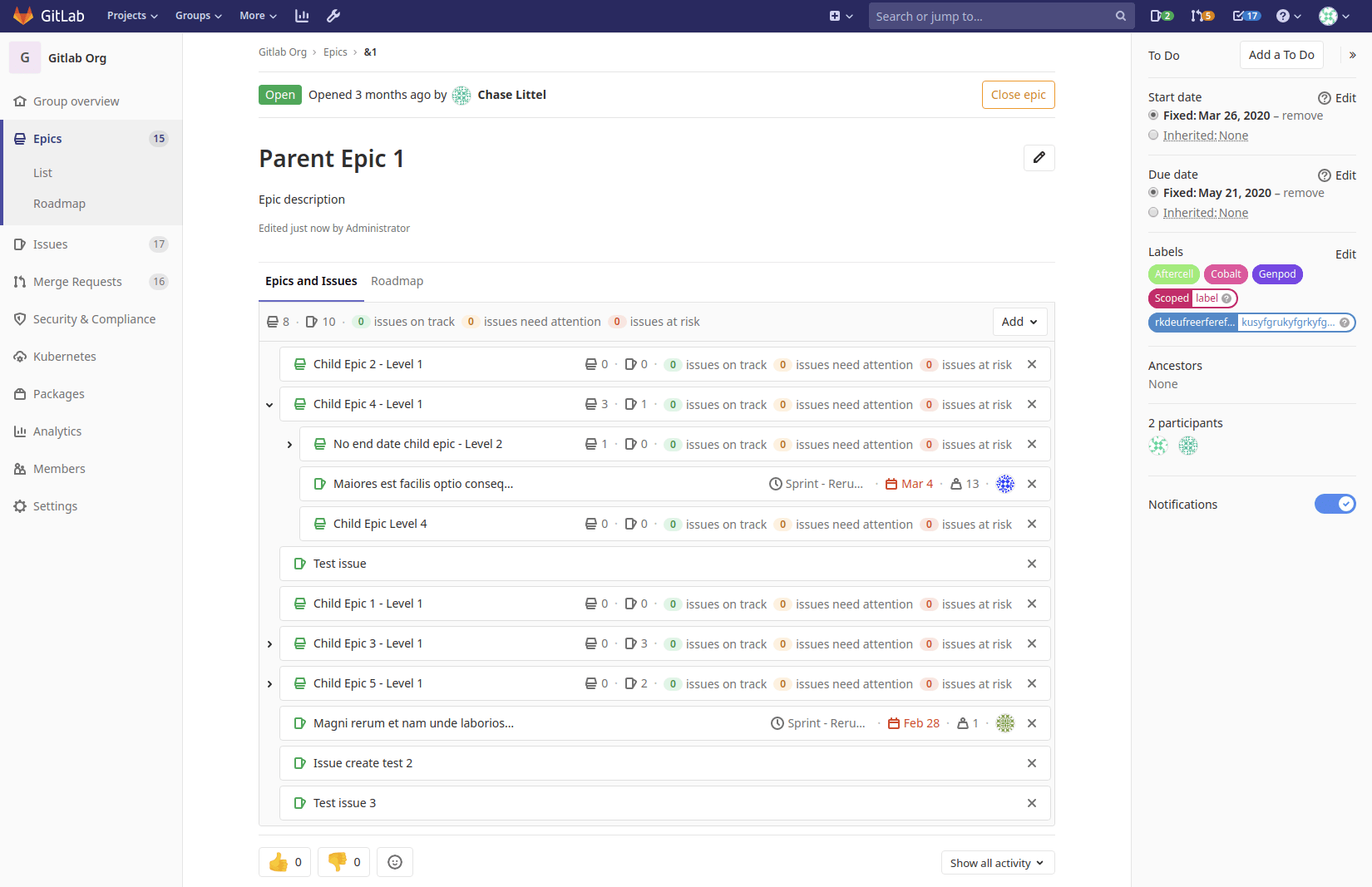
Add latest changes from gitlab-org/gitlab@master
Showing
| W: | H:
| W: | H:


lib/api/entities/freeze_period.rb
0 → 100644
lib/api/freeze_periods.rb
0 → 100644
| ... | ... | @@ -40,7 +40,7 @@ |
| "@babel/preset-env": "^7.8.4", | ||
| "@gitlab/at.js": "1.5.5", | ||
| "@gitlab/svgs": "1.127.0", | ||
| "@gitlab/ui": "14.5.0", | ||
| "@gitlab/ui": "14.10.0", | ||
| "@gitlab/visual-review-tools": "1.6.1", | ||
| "@rails/actioncable": "^6.0.2-2", | ||
| "@sentry/browser": "^5.10.2", | ||
| ... | ... |