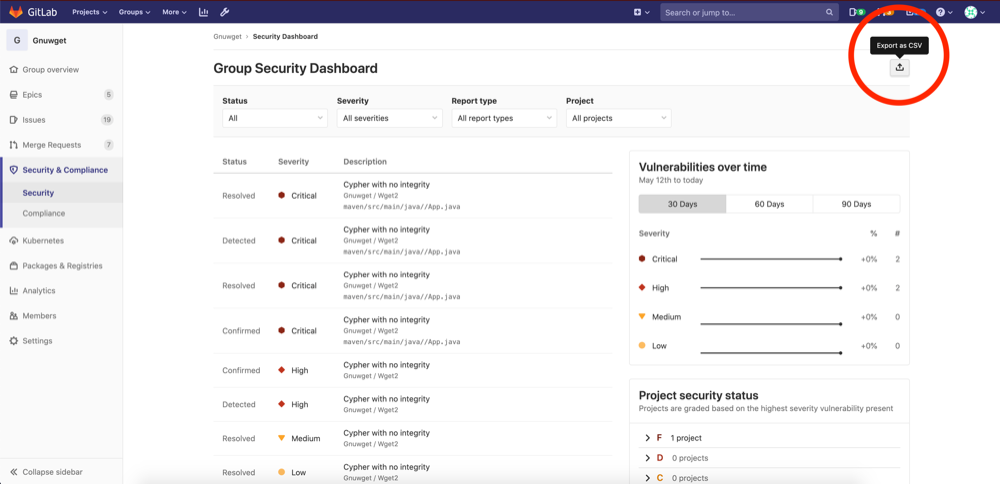
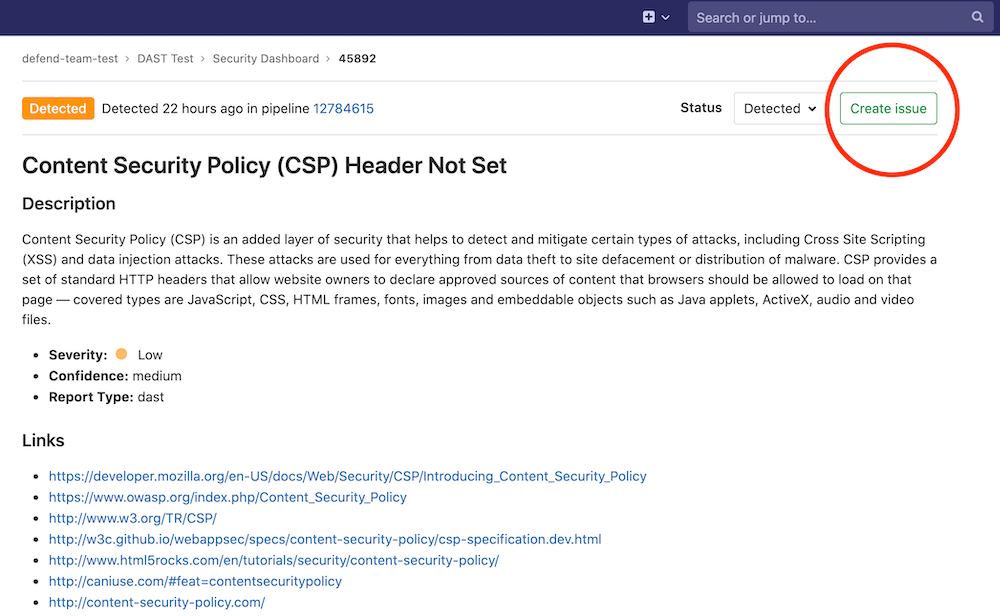
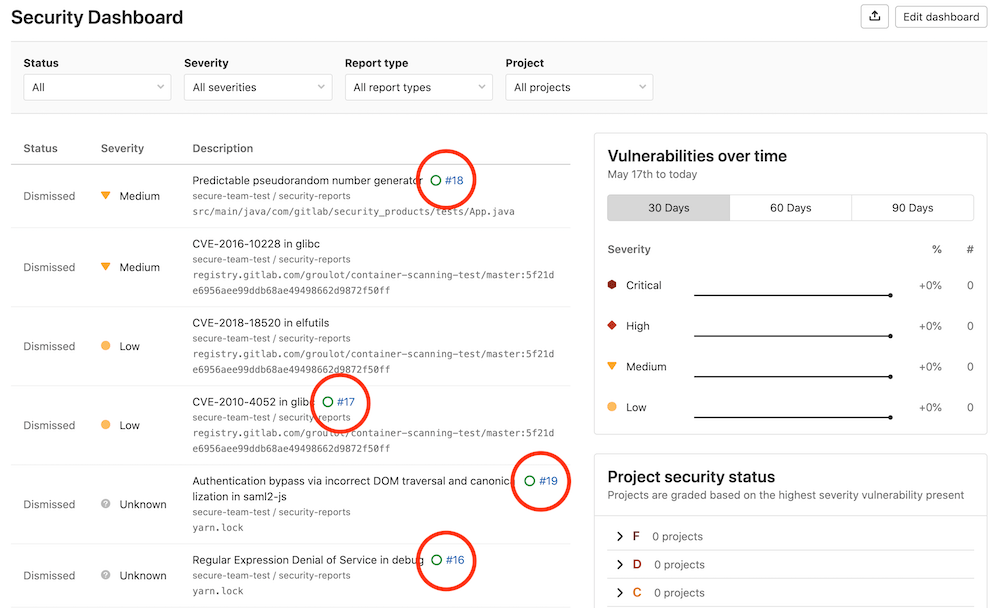
Add latest changes from gitlab-org/gitlab@master
Showing
| ... | ... | @@ -416,7 +416,7 @@ end |
| gem 'octokit', '~> 4.15' | ||
| # https://gitlab.com/gitlab-org/gitlab/issues/207207 | ||
| gem 'gitlab-mail_room', '~> 0.0.4', require: 'mail_room' | ||
| gem 'gitlab-mail_room', '~> 0.0.6', require: 'mail_room' | ||
| gem 'email_reply_trimmer', '~> 0.1' | ||
| gem 'html2text' | ||
| ... | ... |

| W: | H:
| W: | H:


77.5 KB
72.6 KB