Add sample for .NET Core IoT with BMP280 Sensor, Azure SDK and Certificates (#1665)
Showing
71.4 KB
264.7 KB
1.2 MB
36.8 KB
27.6 KB
35.5 KB
25.0 KB
48.2 KB
57.9 KB
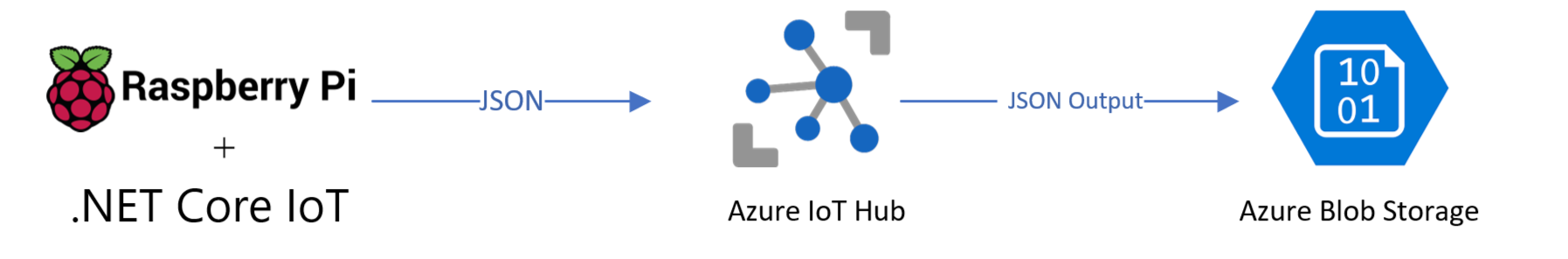
71.4 KB
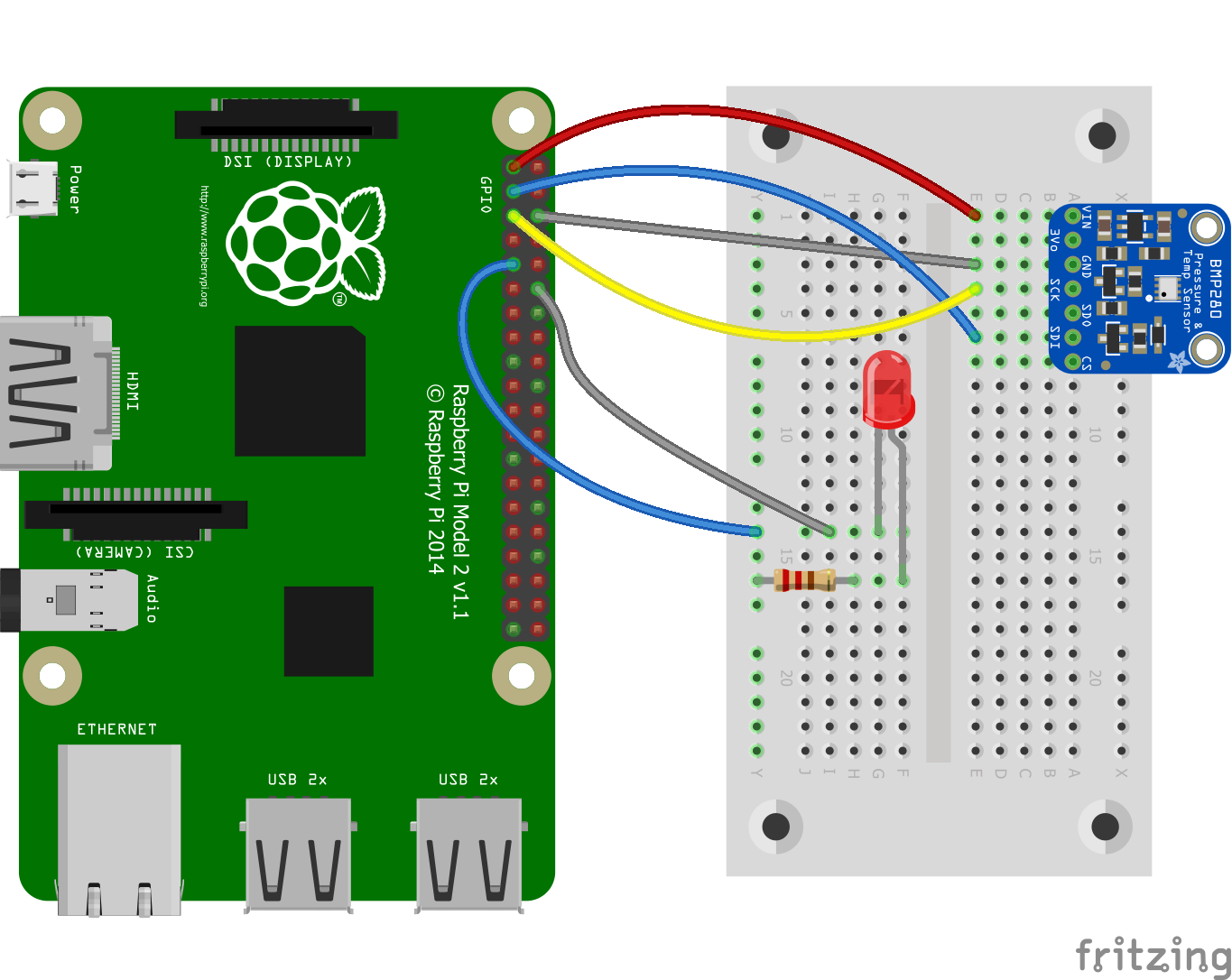
264.7 KB

1.2 MB
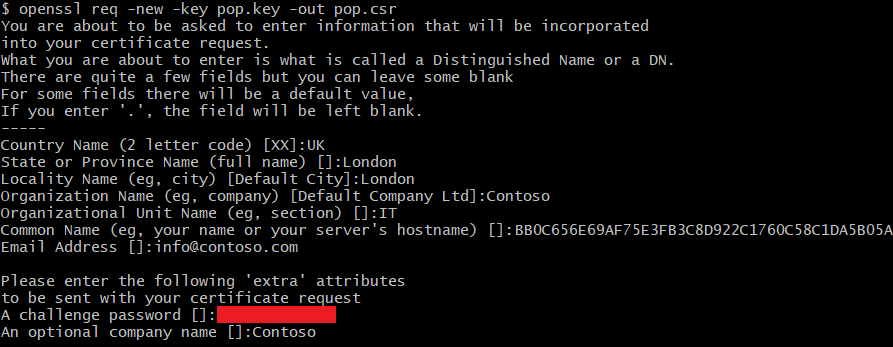
36.8 KB
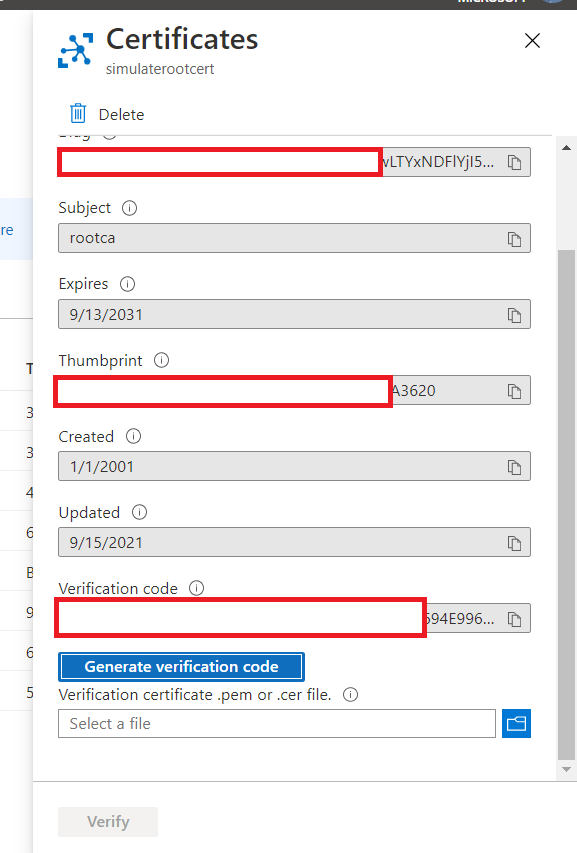
27.6 KB
35.5 KB
25.0 KB
48.2 KB
57.9 KB
