initial version
上级
Showing
.gitee/PULL_REQUEST_TEMPLATE.md
0 → 100644
.gitignore
0 → 100644
LICENSE
0 → 100644
NOTICE
0 → 100644
README.md
0 → 100644
RELEASE.md
0 → 100644
docs/README.md
0 → 100644
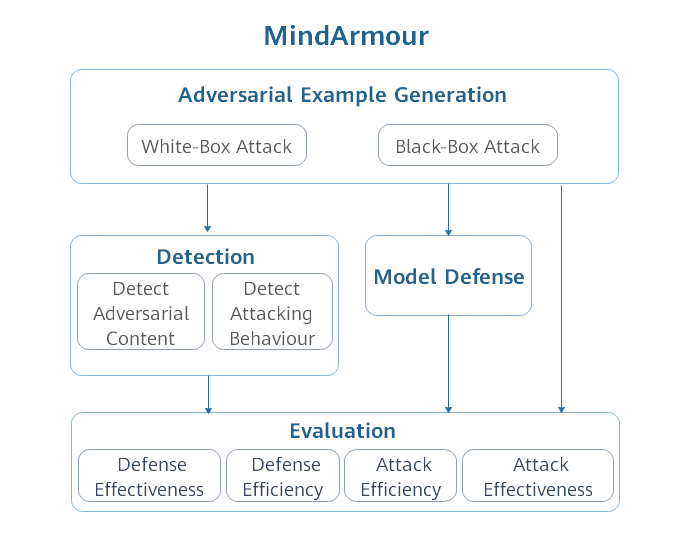
docs/mindarmour_architecture.png
0 → 100644
27.6 KB
example/data_processing.py
0 → 100644
example/mnist_demo/README.md
0 → 100644
example/mnist_demo/lenet5_net.py
0 → 100644
example/mnist_demo/mnist_train.py
0 → 100644
mindarmour/__init__.py
0 → 100644
mindarmour/attacks/__init__.py
0 → 100644
mindarmour/attacks/attack.py
0 → 100644
此差异已折叠。
此差异已折叠。
此差异已折叠。
mindarmour/attacks/deep_fool.py
0 → 100644
此差异已折叠。
此差异已折叠。
此差异已折叠。
mindarmour/attacks/jsma.py
0 → 100644
此差异已折叠。
mindarmour/attacks/lbfgs.py
0 → 100644
此差异已折叠。
mindarmour/defenses/__init__.py
0 → 100644
此差异已折叠。
mindarmour/defenses/defense.py
0 → 100644
此差异已折叠。
此差异已折叠。
mindarmour/detectors/__init__.py
0 → 100644
此差异已折叠。
此差异已折叠。
mindarmour/detectors/detector.py
0 → 100644
此差异已折叠。
此差异已折叠。
mindarmour/detectors/mag_net.py
0 → 100644
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
mindarmour/utils/__init__.py
0 → 100644
此差异已折叠。
mindarmour/utils/_check_param.py
0 → 100644
此差异已折叠。
mindarmour/utils/logger.py
0 → 100644
此差异已折叠。
mindarmour/utils/util.py
0 → 100644
此差异已折叠。
package.sh
0 → 100644
此差异已折叠。
requirements.txt
0 → 100644
此差异已折叠。
setup.py
0 → 100644
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
此差异已折叠。
文件已添加
此差异已折叠。
此差异已折叠。
此差异已折叠。