update docs
Signed-off-by: NAnnie_wang <annie.wangli@huawei.com>
Showing
30.8 KB
21.5 KB
44.7 KB
24.4 KB
62.6 KB
18.7 KB
64.5 KB
18.9 KB
100.1 KB
22.9 KB
150.6 KB
22.3 KB
57.0 KB
文件已移动
Fork自 OpenHarmony / Docs
Signed-off-by: NAnnie_wang <annie.wangli@huawei.com>
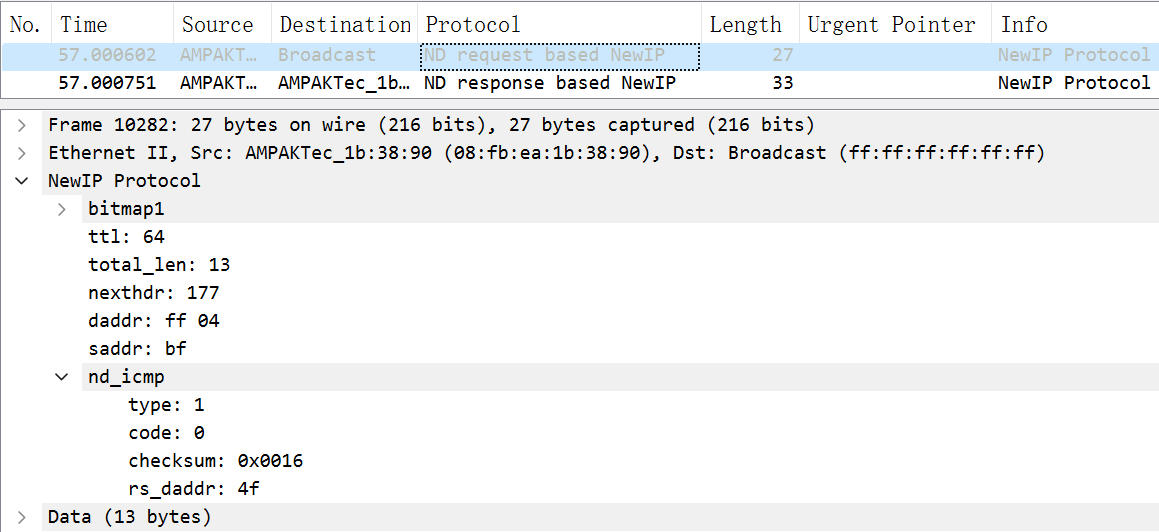
30.8 KB
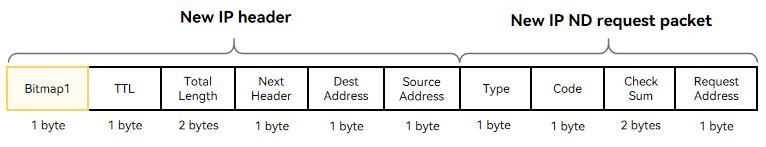
21.5 KB
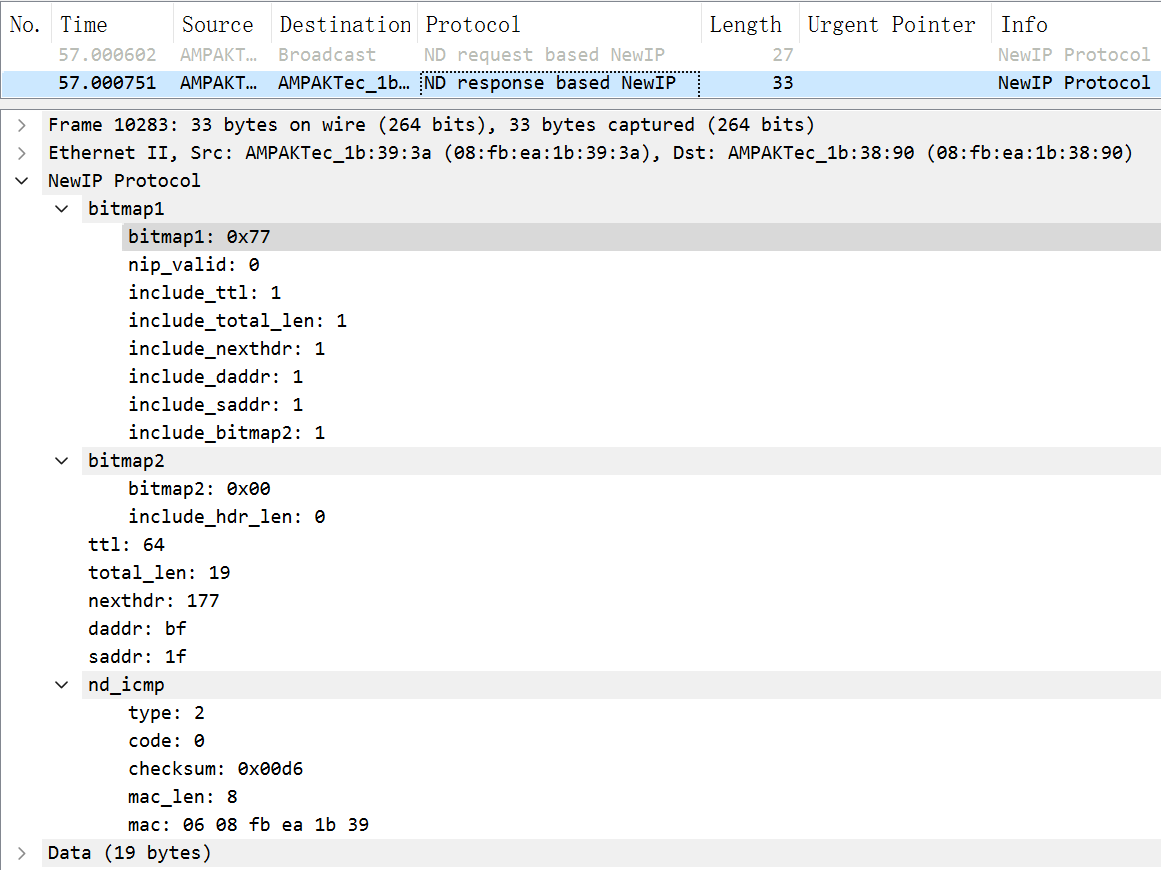
44.7 KB
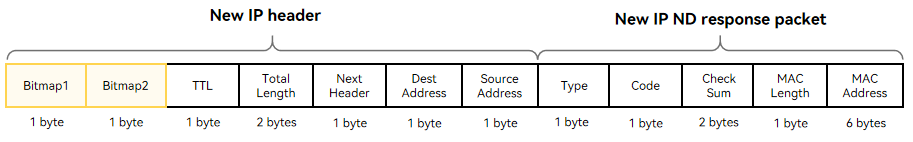
24.4 KB
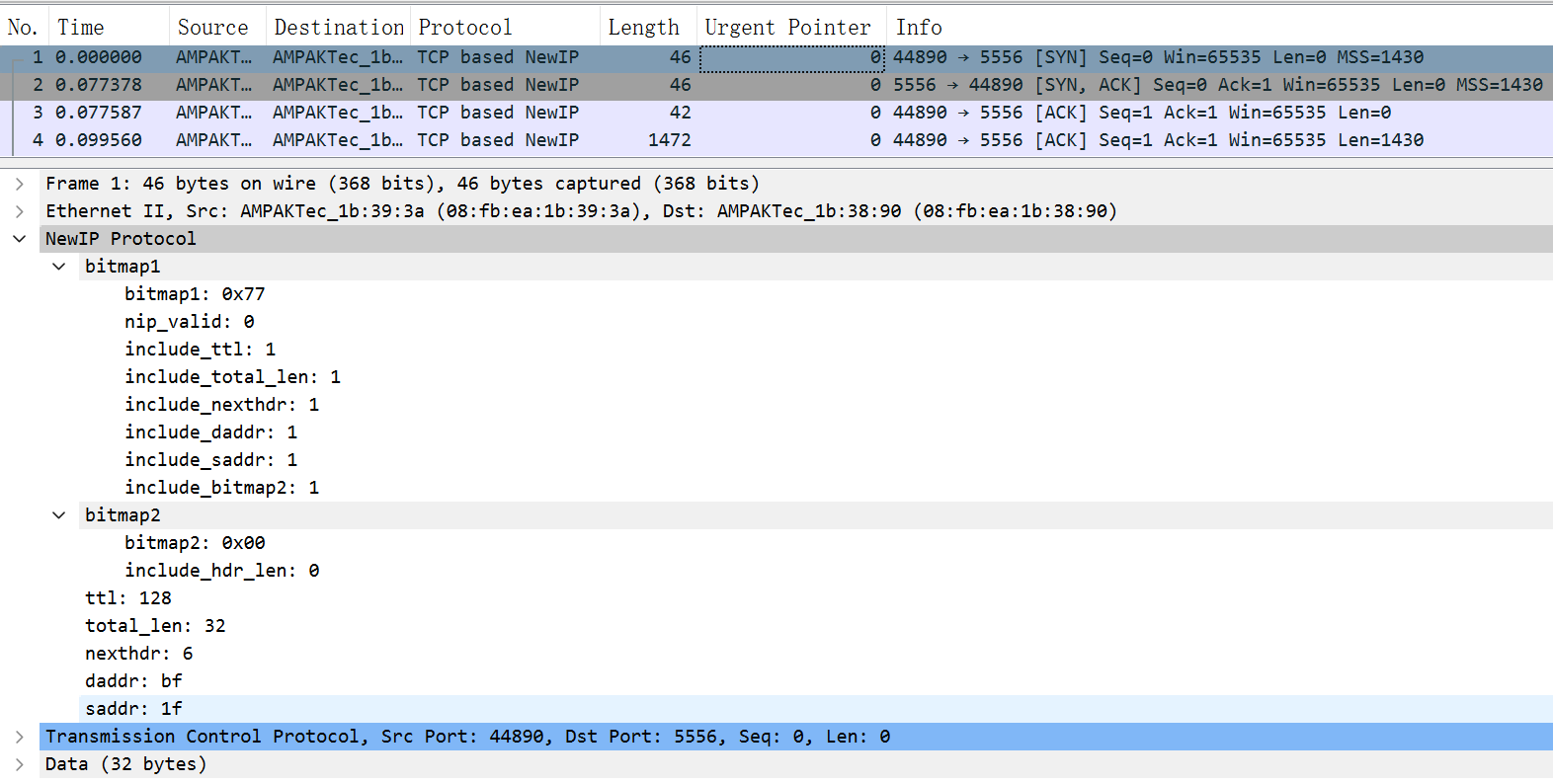
62.6 KB
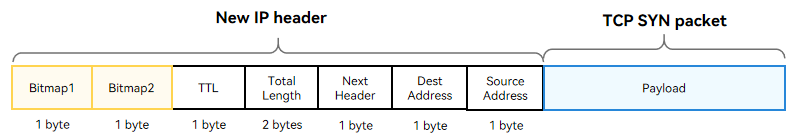
18.7 KB
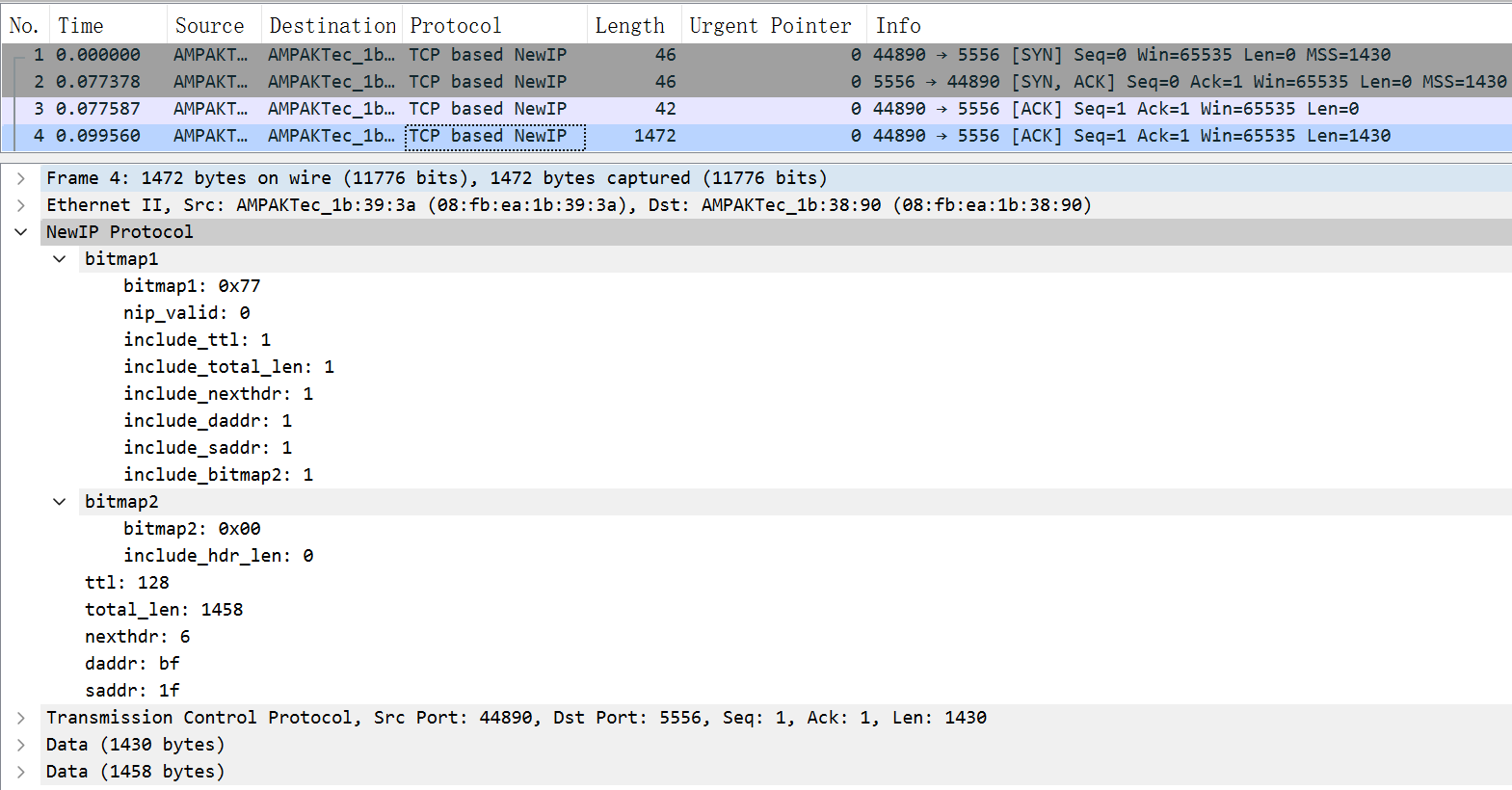
64.5 KB
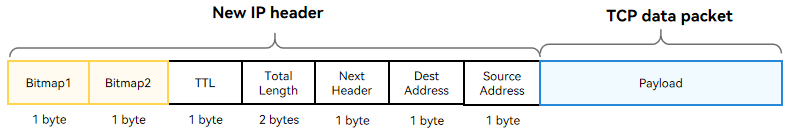
18.9 KB
100.1 KB
22.9 KB
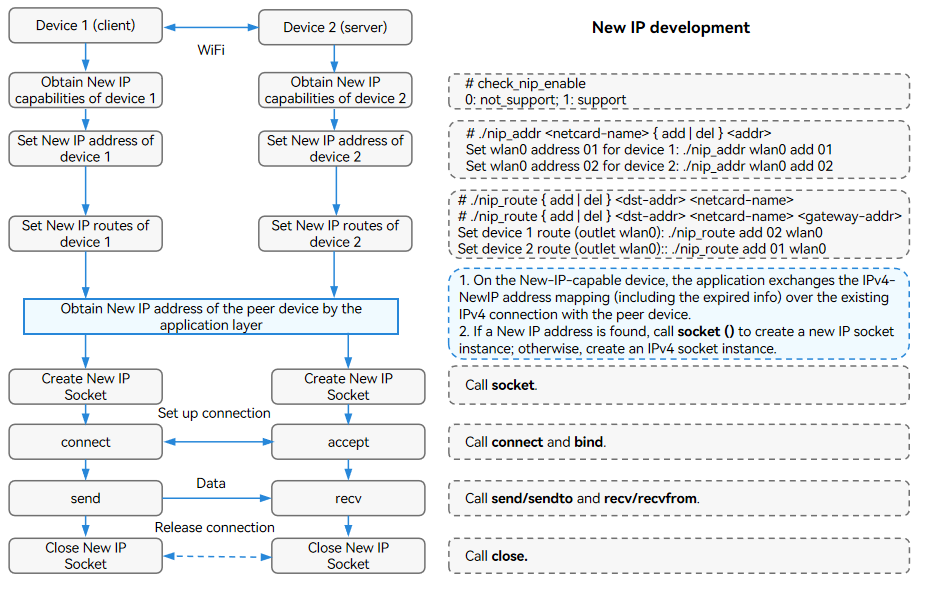
150.6 KB
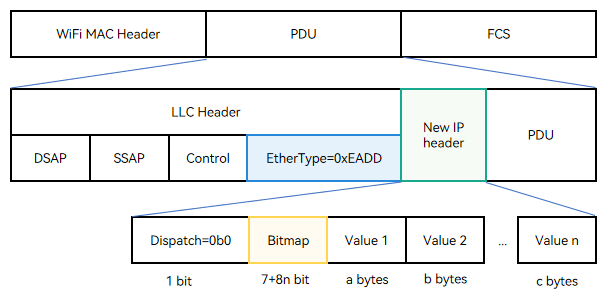
22.3 KB
57.0 KB
